Functional XAT Overview
Access control is composed of three key components: Identity, Role, and Scope. These components together form what is known as an RSI (Role-Scope-Identity) assignment.
Key Components of Access Control
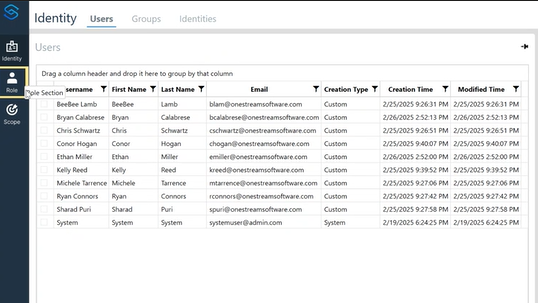
1. Identity
-
An identity can be:
- An individual user
- A group of users
- A group of groups (nested groups)
-
The identity page allows filtering by users, groups, or both.
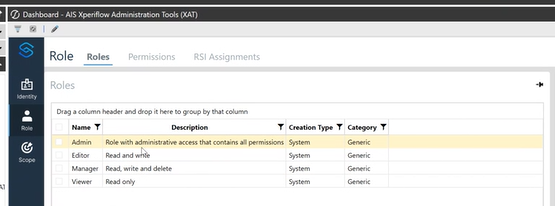
2. Role
-
A role is a container of permissions.
-
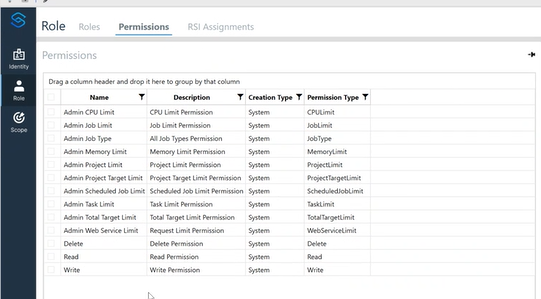
Permissions define what actions an identity can take, such as:
- Read
- Write
- Limitations (e.g., number of projects, CPUs, etc.)
-
XAT comes with predefined roles:
- Administrator – Has all permissions (should be assigned carefully)
- Viewer – Read-only permissions
- Editor – Read and write permissions
- Manager – Read, write, and delete permissions
-
Custom roles can be created:
- Define the role
- Assign specific permissions via the permissions tab
3. Scope
-
A scope defines where a role can perform its assigned permissions.
-
Examples of scopes:
- Project – Permissions apply within a specific project.
- Every time a new project is created, a corresponding scope is created for managing access.
- Global – Permissions apply everywhere.
- Application-specific – Permissions are limited to a specific app (e.g., Development, Production).
- Solution-specific – Permissions are limited to a specific solution (e.g., Data Manipulator, SensibleAI Forecast).
- Application Solution-specific – Permissions are limited to a specific combination of an application and solution.
- Project – Permissions apply within a specific project.
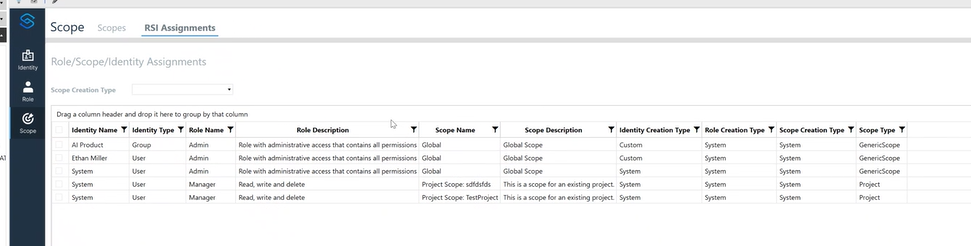
RSI (Role-Scope-Identity) Assignments
-
An RSI assignment ties together an identity, a role, and a scope.
-
RSI assignments can be managed via:
- The role page
- The scope page
-
Viewing RSI Assignments:
- Example: "Ethan has an admin role in the global scope."
-
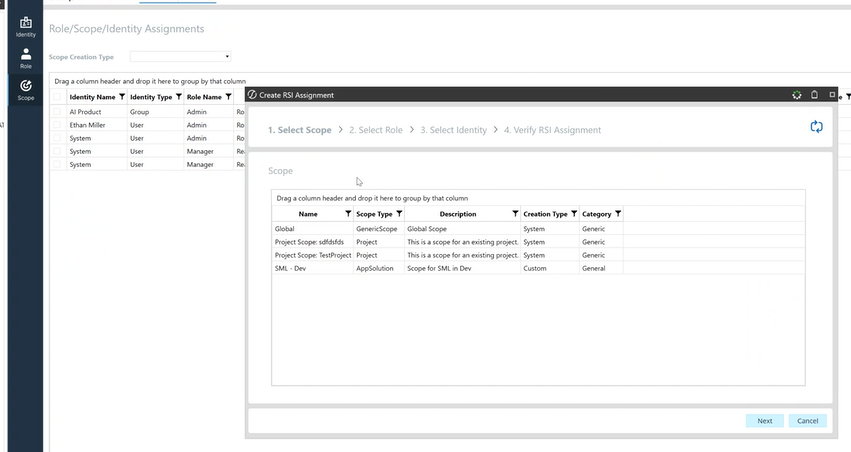
Creating a new RSI Assignment:
- Select a scope (e.g., global scope)
- Select a role (e.g., administrator)
- Select an identity (e.g., Ethan)
- Confirm the assignment.
Types of Permissions
- System Resource Limits - Limits to prevent a single user from overusing system resources.
- Task limits – Maximum number of tasks that can run at once
- CPU limits – Maximum number of CPUs a user can utilize
- Job limits – Maximum number of jobs a user can run or schedule
- Memory limits – Maximum memory usage
- Project limits – Maximum number of projects a user can create
- Project Target limits – Maximum number of targets per project
- Total Target Limits – Maximum number of total targets across all projects
- Web service limits – Controls API request rates
This is a list of the permission types available. You can create custom permissions based on the permission types.
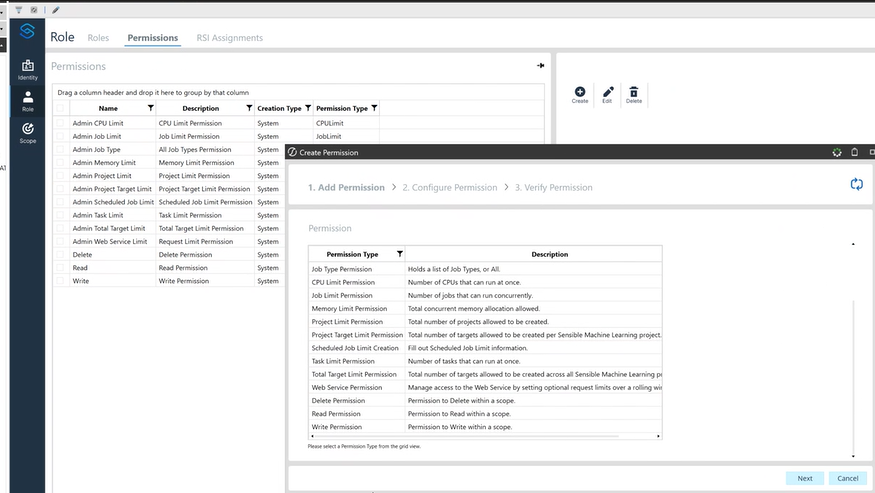
2. Job Type Permissions – Determines if a user can run specific job type.
Basic permissions:
- Read – Can view the resource
- Write – Can modify the resource (e.g., submit a job)
- Delete – Can remove the resource
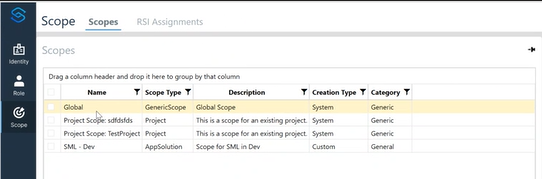
Scope Types
- Application Scope – Controls access within a specific app.
- Solution Scope – Defines permissions for a combination of applications.
- Project Scope – Access control for specific projects.
- Global Scope – Permissions apply across all scopes globally.
Summary
Access control in A1 Cellular Access Control is structured around Identity, Role, and Scope. By combining these elements into RSI assignments, organizations can finely tune permissions and access levels within their environments.
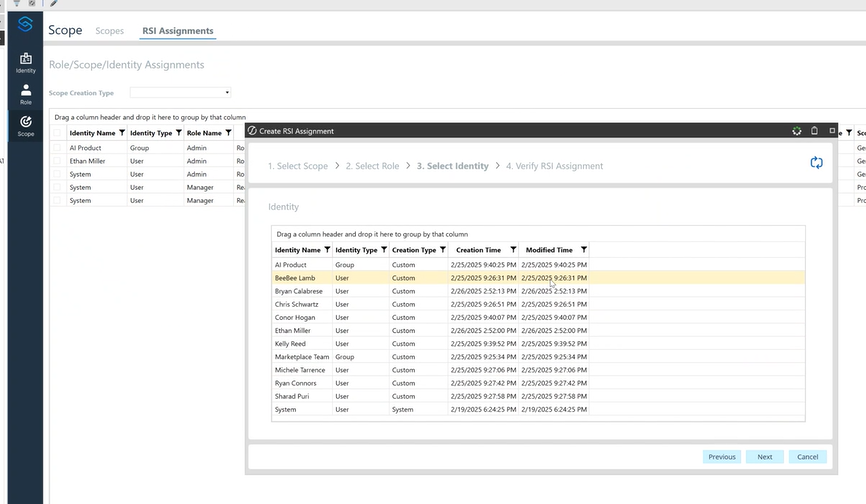
RSI Assignment/Permissions
After identifying your roles/scopes/identities, you can create your RSI assignments. Below is a walkthrough of what this may look like combining scope, role and identity to create the RSI assignment.
Generate RSI Assignment:
Establish Scope:
Assign Role:
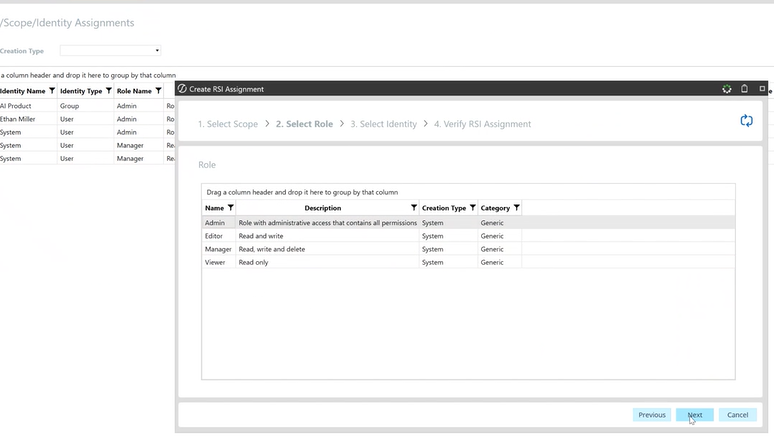
Assign Identity: